The convenience of a smart home is undeniable, but it comes with an inherent risk: cybersecurity. The thought of your connected devices, from smart locks to cameras, falling into the wrong hands is unsettling. If you suspect your smart home has been compromised, acting swiftly and decisively is paramount. Understanding the immediate steps to take and, crucially, investing in a robust network foundation are your best defenses. For a comprehensive overview of protecting your digital fortress, consult our Ultimate Smart Home Security Guide.
While recovering from a hack involves several steps, a key aspect of both prevention and recovery lies in your home network’s backbone. A high-performance, security-focused router is not just about speed; it’s your first line of defense against unwanted intrusions and a critical tool for segmenting your network and monitoring traffic.
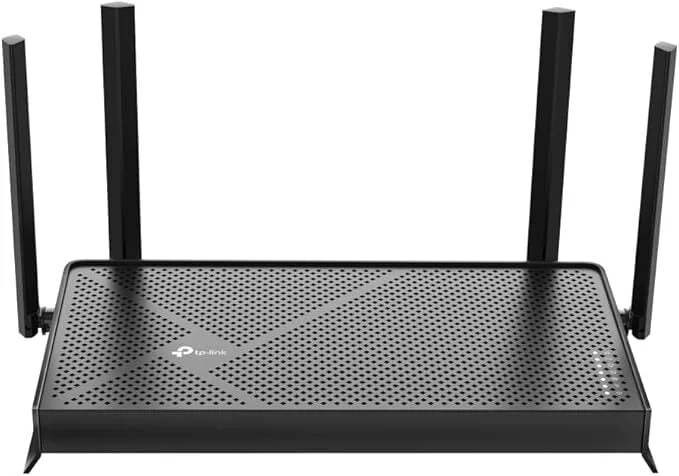
TP-Link Archer AXE75: In-Depth Analysis
Key Considerations for Smart Home Security and Recovery
If your smart home has been compromised, or you want to prevent it, understanding these foundational principles is essential. Your router plays a pivotal role in each of these areas.
Immediate Actions After a Suspected Hack
The moment you suspect a hack, immediate isolation is key. Disconnect the compromised device from the network, change all associated passwords (router, device accounts, Wi-Fi), and perform a factory reset on the device if possible. Your router’s administrative interface will be crucial here for changing Wi-Fi passwords and reviewing connected devices. Consider temporarily disabling internet access for suspicious devices via the router’s settings.
Prioritizing Network Segmentation for Smart Devices
One of the most effective ways to mitigate the damage of a smart home hack is network segmentation. This involves creating separate networks for different types of devices. Many modern routers, like the TP-Link Archer AXE75, offer guest network functionality, which can be repurposed for IoT devices. This isolates them from your primary network where your computers and personal data reside. If an IoT device is compromised, the attacker is contained within that segregated network, unable to easily access more sensitive parts of your digital life.
The Importance of Strong Passwords and Multi-Factor Authentication (MFA)
This cannot be stressed enough. Weak, default, or reused passwords are the easiest entry points for hackers. Use unique, complex passwords for every smart device, router, and associated cloud service. Enable Multi-Factor Authentication (MFA) wherever available. While not directly a router feature, your router’s security depends on a strong admin password, and it enables the secure connections that MFA relies upon.
Regular Firmware Updates and Security Monitoring
Software vulnerabilities are a common vector for attacks. Ensure all your smart devices, and especially your router, are running the latest firmware. Manufacturers frequently release updates that patch security holes. Additionally, regularly check your router’s logs for unusual activity or unauthorized connections. Many modern routers offer features like intrusion detection systems or real-time protection, as seen with TP-Link’s HomeShield, which can alert you to suspicious behavior.
Final Verdict
Dealing with a smart home hack can be stressful, but by taking immediate action and building a resilient network, you can significantly reduce your risk and recover more effectively. The TP-Link Archer AXE75 exemplifies the kind of advanced networking hardware that forms the bedrock of a secure smart home. Its robust security features, tri-band Wi-Fi 6E capabilities, and intelligent management tools make it an excellent investment for anyone serious about protecting their connected living space. Remember, proactive security measures and a strong network foundation are your best allies in the evolving landscape of smart home cybersecurity.